Mobile Device / Security Review
Protect yourself before you wreck youself
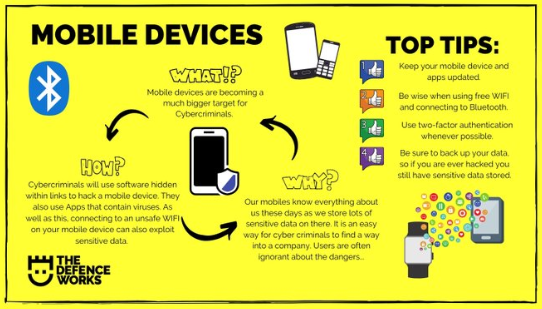
What’s a Mobile Device?
Mobile devices — which include not only smartphones but also smart watches, tablets, notebooks, and laptops — are any portable electronic equipment that can connect to the internet.
One of the biggest security challenges for NC State University is cybercrime — especially when malicious hackers target our mobile devices.
What the Pack Can Do
NC State needs every one of us to secure all our mobile devices.
NC State’s Office of Information Technology requires minimum security controls, and although critical, they are not always enough. Without securing our mobile devices, cybercriminals are afforded countless opportunities to routinely hack into enterprise systems by exploiting the users who fail to comply with specific cybersecurity requirements — which can result in data breaches that leak sensitive information belonging to you and others, and subsequent substantial fines and legal costs to the university.
The cybersecurity team at NC State University has researched and assembled the most effective procedures known to protect your data from malicious hackers. To create and maintain a truly secure mobile device — one that protects you and the pack from cybercrime — you can invest a relatively small amount of time to prevent catastrophic loss to you and the pack.
Secure your device!
- Physically secure your device.
Don’t leave any of your devices unattended. Theft of mobile devices is one of the most common ways that data is stolen. The NC State Help Desk regularly receives reports of device theft from vehicles. - Secure all future data.
Enable lost-device functionality. Configure the device settings to automatically wipe all data after a particular number of incorrect logins are attempted (for example, 10); also, enable the option to wipe the device remotely. - Provide ongoing physical protection.
Use only trusted chargers and cables. Do not use public charging stations. A malicious charger or computer can load malware onto mobile devices via the charging station. Such malware can circumvent your device protections and even take control of them. A device infected with malware can propagate infections to other devices. - Power down often.
Power the device off and then power it back on frequently, at least once a week. Doing so can help prevent malware installation and zero-click exploits. - Avoid phishing attempts.
Never click a link or open an attachment from someone you don’t know, and make sure every sender’s email address is exactly as it should be. For example, if you have a friend with the email address of joesample@gmail.com, don’t trust an email from Joe Sample with an email address joesamp1e@gmail.com where the number one (1) replaces the letter “l”. - Don’t use text messaging for sensitive content.
When a website prompts you to receive a passcode, never opt for a passcode via text messaging. - Connect your new device to eduroam.
The eduroam service is NC State’s only secure wireless service that encrypts your data in transmission. As an added benefit, enrolling in eduroam at NC State allows you to connect to secure Wi-Fi automatically at participating educational and research institutions worldwide. - Apply security updates.
Manufacturers and application developers update their software to fix bugs and vulnerabilities. Apply these security updates as soon as possible to ensure you’re fixing identified weaknesses. - Be careful when downloading apps.
- Make sure you trust the app providers and download apps only from trusted sources such as the Google Play Store or Apple App Store, as they are more proactive about removing malicious apps.
- Limit the amount of personally identifiable information you share with each app. Also, allow each app to access your location only while actively using the app.
- Beware of free public Wi-Fi.
Always assume cybercriminals are nearby and ready to attack wherever public Wi-Fi is available; avoid performing any sensitive activity like a bank transaction on public Wi-Fi. If you need to access your Unity account, disable any unsecured Wi-Fi and switch to your mobile network. If this is not a suitable option and you must use public Wi-Fi, use it only over the NC State Virtual Private Network. - Disable unwanted and unnecessary services.
Capabilities such as Bluetooth, Near Field Communication, unsecured Wi-Fi, and GPS provide convenience, but they can make it easier for a nearby, unauthorized user to access your data. Turn these features off when you are done using them.
Check for Chrome and other browser updates every time you open a browser.
Make it a habit to update your Chrome browser as soon as updates become available. The sooner you update your browser, the better the protection for your device and its data.
Origami Risk Software
A New Incident Intake Process Unfolds!

Insurance and Risk Management implemented a new software, Origami Risk, in June 2022. This software allows IRM to collect more data on incidents and claims. Currently, Origami is structured to collect Automobile and Property related incidents and claims. In the coming months, we will add Liability incidents to Origami. In the second half of the year, we will add the rest of our claims to Origami’s Incident Intake Portal.
How do I report an incident?
- Use this link and choose the type of incident you wish to report. Even if you do not think it will turn into a claim, this will allow IRM to review and better support you.
Who should report an incident?
- Anyone can submit an incident, you do not need NCSU credentials
- Since many EHPS staff are first responders, please fill out our incident intake form or share the link with those involved so we can better support our campus partners
Why should I report an incident?
- Quicker IRM and campus partner response times – the incident intake form alerts IRM staff and collects all pertinent information IRM needs to submit claims to insurance companies
- Increase IRM awareness of incidents in order to run trends analysis and better mitigate future losses
When should I report an incident?
- As soon as safely possible following an incident. It is easier to provide information when it is fresh in the mind immediately following an incident
Lucidspark/Lucidchart
Swimlanes – are not just for pools
Lucidspark is a collaborative space product where you work with your colleagues to share processes, work flows, or just to whiteboard ideas. The key word being ideas, this is where Lucidspark shines, bringing together people into a collaborative space to bring out ideas into a shared space.
Lucidchart is an organizational tool for diagramming and showcasing a detailed process. Ever wanted to dip your toe into visualizing which processes are owned by whom? Lucid chart has a solution for you, swimlanes. Swimlanes are a container that you add to your documentation to delineate who owns what processes. No longer are swimlanes just for pools.
Spotlight
Other Campus Newsletters

Campus offers other great periodic emails! Check out below a selection from our friends!
